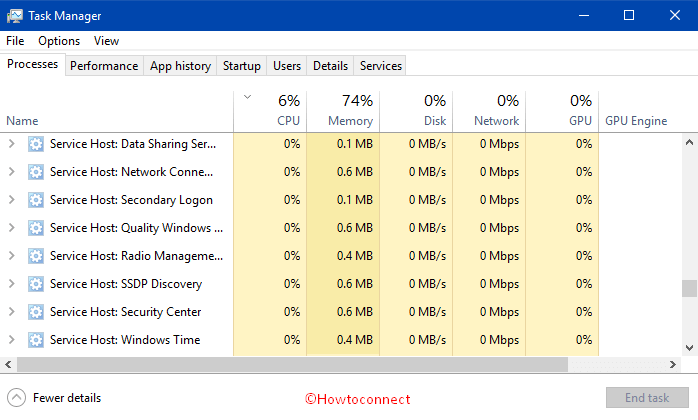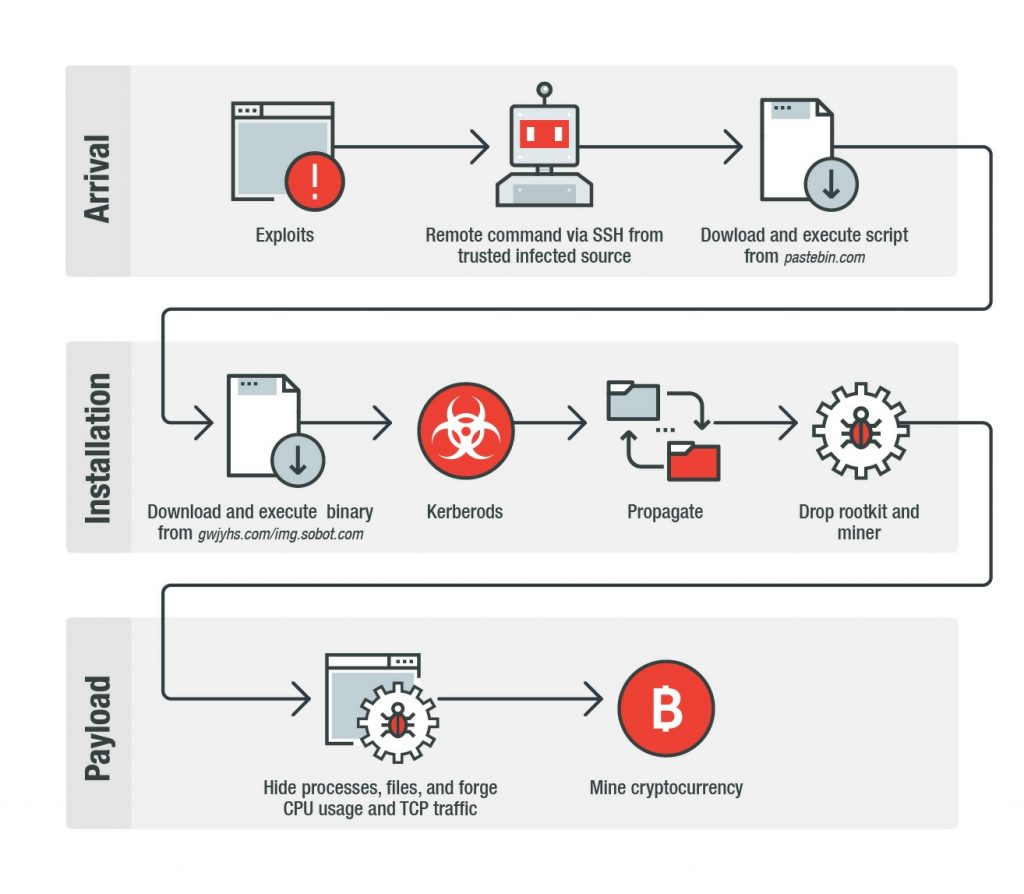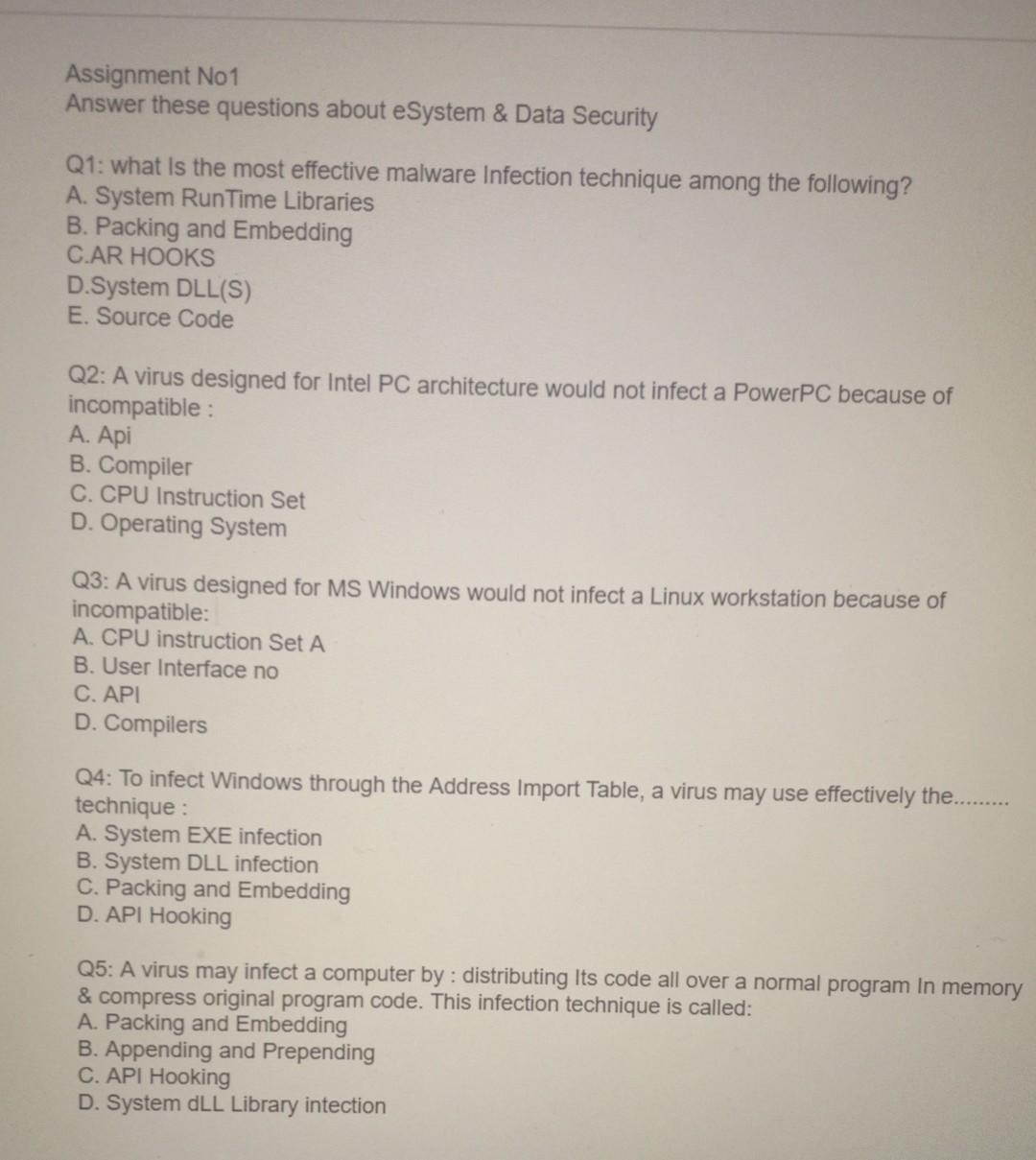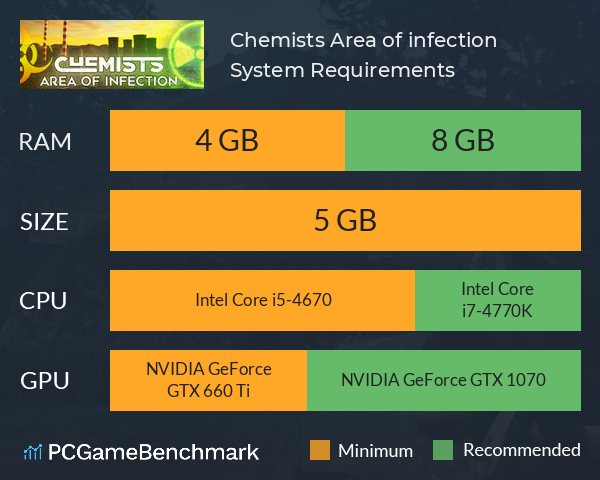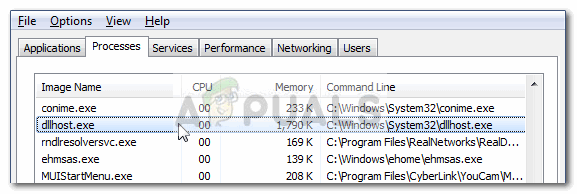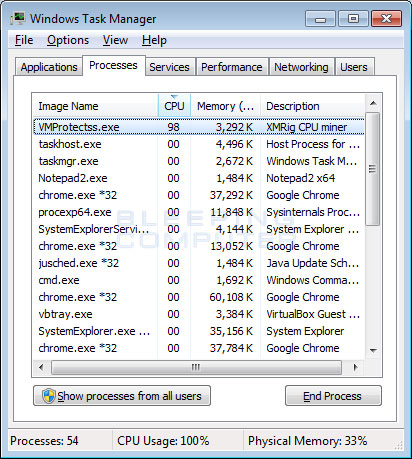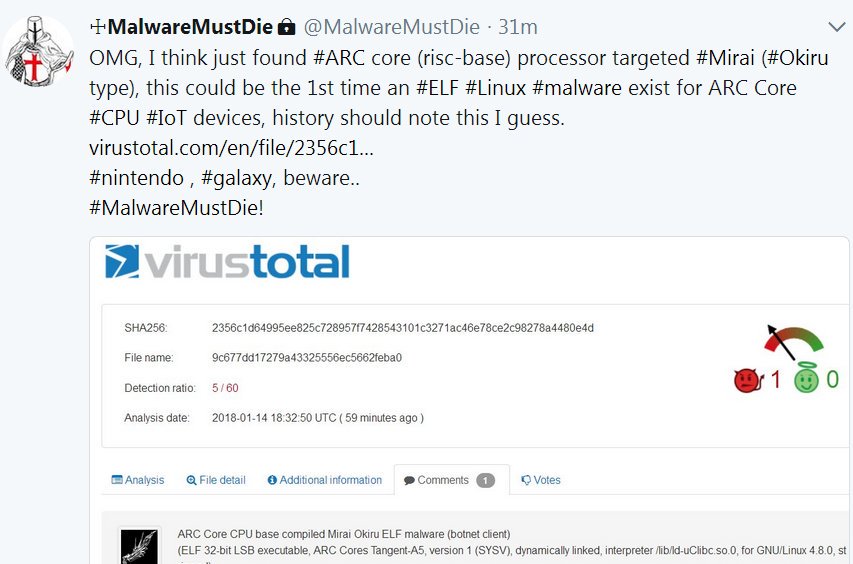
Odisseus on Twitter: "From this day, the landscape of #Linux #IoT infection will change. #ARC cpu has produced #IoT dervices more than 1 billion per year. So these devices are what the
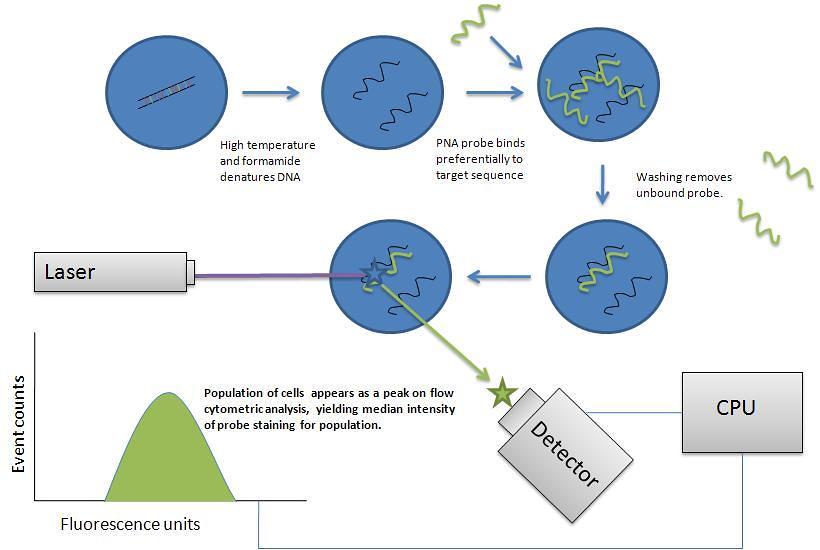
Peripheral blood cell-specific cytokines in persons with untreated HIV infection in Malawi, Africa | Jason and Jarvis Associates, LLC

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

CPU Virus Infection Spreading Across the Motherboard Stock Illustration - Illustration of connecting, power: 134355324

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy

PDF) Usefulness and problems of the urinary tract infection criteria for evaluating drug effi cacy for complicated urinary tract infections | Katsumi Shigemura - Academia.edu

Valnoctamide Inhibits Cytomegalovirus Infection in Developing Brain and Attenuates Neurobehavioral Dysfunctions and Brain Abnormalities | Journal of Neuroscience

Cpu On Board With Cyber Attack And Skull Hologram Stock Photo - Download Image Now - Blue, CPU, Computer - iStock

Cyber attack and skull glowing hologram over working cpu in background. Danger alert, threat, infection and warning abstract concept with skull symbol Stock Photo - Alamy